
Cybersecurity Threats in 2025: The Digital War We Can’t Afford to Ignore
August 13, 2025Growing Cybersecurity Threats
Cybersecurity threats are becoming one of the most critical problems of our connected era. Our digital world is doing well in 2025. The future is here: cloud-based companies, AI assistants, and smart houses. But even as we take interest in invention and seamless connectivity, a more sinister trend is developing in the background: cybersecurity risks.
These threats are no longer the outcome of individual hackers. They belong to an advanced cybercrime ecosystem that is more rapid, intelligent, and hazardous than anything we have ever seen. Due to undetected data theft and billion-dollar ransomware attacks, the battleground has changed and the risks are quite high.
Why Traditional Security Measures Fail Against Cybersecurity Threats
Cybersecurity threats are constant and changing in this day and age. Standard security measures are simply insufficient. Ten years ago, a firewall and antivirus software would have been enough, but today’s attacks can use artificial intelligence (AI), social engineering, and real-time manipulation to compromise even the most advanced systems.
Online threat protection is becoming a significant responsibility, and not only for huge organizations. Nowadays, startups, hospitals, schools, and even individual devices are targets. Hackers want control, disruption, and data power in addition to financial gain.

The Threat of Deepfakes and AI-Powered Phishing
The emergence of deepfake technology and AI-generated phishing emails shows how cybersecurity threats are becoming almost unnoticeable from everyday activity. Attackers mimic rather than just break in. They are invisible. And the harm has already been done by the time you recognize a problem.
Organizations must implement multi-layered threat defense measures to prevent this. This includes advanced threat detection software that changes with attackers, identity verification systems, and behavior-based monitoring.

But technology alone cannot achieve everything. The human factor remains the greatest weakness. One careless click. One password that was used again. One unsuspicious download. That is all it takes to enable a complete attack. For this reason, reaction playbooks, real-world simulations, and personnel training are vital components of cyber security and threat management.
This is preparation, not paranoia.

Meanwhile, businesses are upgrading and investing in powerful cyberattack defenses that identify attacks rather than simply responding to them. AI-powered systems can now identify minute changes in user behavior, isolate malicious devices immediately, and prevent attacks in seconds. Addressing today’s cybersecurity threats needs this level of reliable protection.
It’s important to think about network security threats and solutions. A single unpatched router, an unmaintained Internet of Things device might operate as a weak link in an otherwise strong protective system.
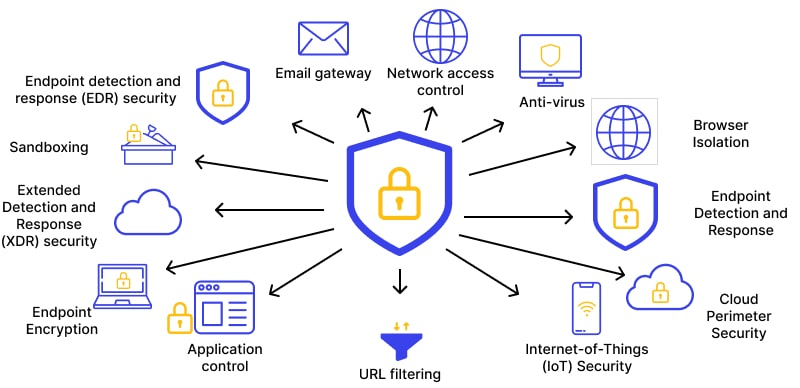
The Importance of Endpoint Protection
Cybersecurity endpoint protection is another crucial element in today’s environment. Any laptop, tablet, or smartphone that is linked to a network becomes a possible point of entry for hackers. You’re not protecting a fortress if you don’t have proper endpoint security; instead, you’re leaving the gates open.

The Good News: Cybersecurity Tools Are Evolving
The good news? We are not powerless. The development of top cyber security solutions has given businesses the tools they need to fight back and win. These technologies, which provide real-time insights, automated threat response, and complete analytics, assist firms in identifying risk factors and developing solutions.
Ignoring cybersecurity risks is no longer an option as how dependent we are on technology in anything from healthcare to banking increases. Threats are genuine. The dangers are getting more serious. However, we can hold on our lead provided by the right resources, instruction, and mindset.
Because cybersecurity in 2025 requires more than just protecting technology and it also involves maintaining confidence. In this age of technology, trust is crucial.

Great impressive 👍